A few days ago, news broke about a large-scale hack of various sites by the Syrian Electronic Army. The motivation behind the hack was political and the only damage came down to a popup message: “You’ve been hacked by the Syrian Electronic Army (SEA).”.
Happy thanks giving, hope you didn't miss us! The press: Please don't pretend #ISIS are civilians. #SEA pic.twitter.com/ZXzMWbXoYp
— SyrianElectronicArmy (@Official_SEA16) November 27, 2014
Reports claim this hack affected about 600 large sites, including some major ones such as Dell, Microsoft, Verizon Wireless, Wallmart Canada, NBC and more.
https://twitter.com/i_c_e4/status/538043815480025089
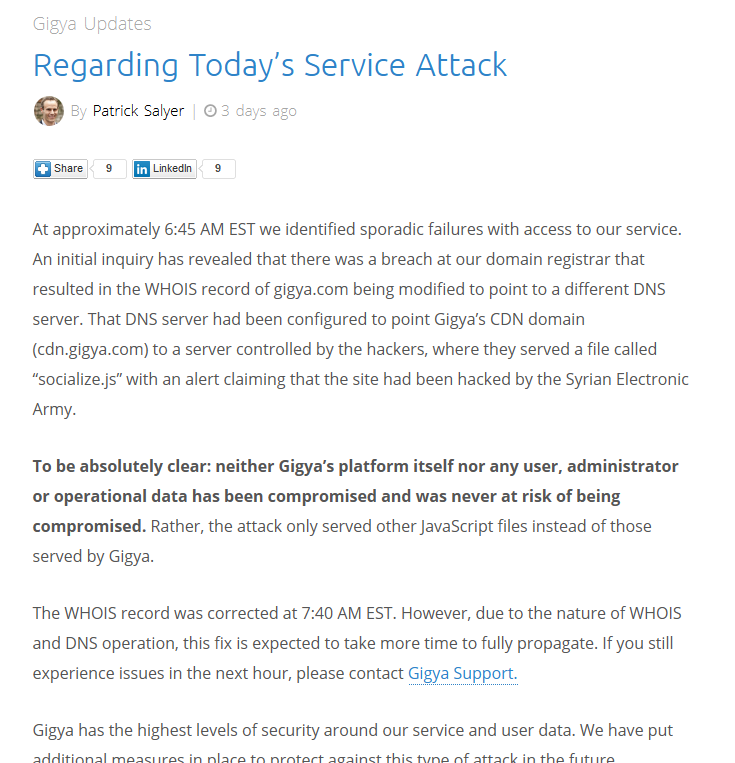
The SEA didn’t hack into all those sites one by one. Instead, they hacked into one SaaS provider, Gigya, affecting all its customers. Gigya defines itself as an “identity management platform” and they offer websites with features such as social login. Gigya’s platform deals with users and as such, stores and processes personally identifiable information.
As described in the media and confirmed in Gigya’s blog, SEA managed to get control of Gigya’s Godaddy account, which resulted in a redirection of Gigya’s assets to SEA controlled services.
This is a very unfortunate turn of events. I feel sorry for Gigya’s team and investors. Gigya doesn’t seem like a company that disregards security completely. Their data security page, though marketing-oriented, does mention an ISO 27001 certification. However what I found amusing is Gigya’s CEO response to the incident on Gigya’s official blog.
It is now absolutely clear to me that “neither Gigya’s platform itself nor any user, administrator or operational data has been compromised and was never at risk of being compromised. Rather, the attack only served other JavaScript files instead of those served by Gigya.“. This statement is fairly accurate, however, it fails to mention that though Gigya’s infrastructure has not been compromised, all of Gigya’s customers’ websites were compromised to some degree. With all due respect, JavaScript files ARE IMPORTANT. Having control of a website’s JavaScript files means control of the site’s client-side functionality.
In fact, the main reason Gigya’s platform was not compromised was because it was down at the time of the hack. If the attack was more selective, then Gigya would have been compromised too, simply because Gigya is “eating its own dog food” and using the service itself for login. There is also place to wonder how SEA managed to get access to Gigya’s Godaddy account without compromising any user accounts at Gigya. I wish I had more information. This could turn out to be Godaddy’s fault as well.
What I do know is that this incident might have the best outcome for Gigya out of all possible scenarios. Imagine what interesting attacks one could have made if this hack was performed by cyber criminals. An obvious one would have been to bundle an exploit to the regular payload and hijack the computers of millions of visitors to Gigya enabled sites. I am sure one can make millions, if not hundreds of thousands of USD this way. A less obvious one would be to bundle malicious code to hijack login pages, capture login credentials and send them to a third-party. With Gigya being a social login platform, I expect millions of Facebook, Google and other accounts can be hijacked this way without any exploits. This might be happening somewhere on the Internet as we speak. In fact, I believe SEA are aware of the potential impact, when they say:
We're the good guys so this was harmless but just in case the bad guys copy us, use NoScript with Firefox: https://t.co/TawKevraTo #SEA
— SyrianElectronicArmy (@Official_SEA16) November 27, 2014
It is a good advice by SEA, unfortunately using NoScript is a pain, and most visitors will not bother. Plus, I wonder if you can use any of the affected sites without JavaScript or without Gigya’s login.
This is not the first time we see attacks on SaaS providers. SEA itself already hacked two other similar companies in the past; Outbrain and Taboola. Attacks on service providers are very attractive to hackers due to the massive impact they can create. With the adoption of SaaS and the rising concern for cyber-attacks, companies have to be cautious of the third-parties they engage. Because SEA is a political organization, they make sure to spread the word about what they do. On the other hand, other such attacks might be happening around us, without us knowing, simply because criminal attackers have all the incentives to keep things secret.
Unfortunately we don’t know the exact actions SEA took to take over Gigya’s Godaddy account, still if you are managing valuable domains, and would like to protect them against potential hijacking follow these guidelines:
- Protect the entire chain of access to your assets. Including domain registration, DNS, CDN, hosting, application, etc.
- Use two-factor authentication where possible. Funny enough, Godaddy only offers such protection to customers with a US address.
- Use strong, random passwords.
- Use unique usernames and email addresses for key accounts.
- Don’t use “password reminder question”, or if you are in the mood, use “Dear hacker, what is the random number I used?”
- Be careful about phishing emails. At least 2 out of 3 SEA hacks were a result of phishing campaigns.
- Make sure your systems are updated against security vulnerabilities.
- Use HTTPS and HTTP Strict Transport Security with your resources to prevent somebody from taking over them.